PGP_PublicEncrypter – Global Encryption Element
In this case we are using our Secret Key, Secret Alias ID, and Secret Passphrase to sign the encrypted message. We use the recipient’s (in this case “Joe Bob”) Public Key and Principal Email.
PGP_PrivateDecrypter – Global Encryption Element
Global Elements:
<encryption:config name="PGP_PublicEncrypter"
defaultEncrypter="PGP_ENCRYPTER"
doc:name="PGP_PublicEncrypter">
<encryption:pgp-encrypter-config
principal="Joe Bob
<jobbob@yahoo.com>"
publicKeyRingFileName="C:\vault\keys\joebob_public.gpg"
secretAliasId="-4553241976692078076"
secretKeyRingFileName="C:\vault\keys\my_secret.gpg"
secretPassphrase="MySecretPass"/>
</encryption:config>
<encryption:config name="PGP_PrivateDecrypter"
defaultEncrypter="PGP_ENCRYPTER"
doc:name="PGP_PrivateDecrypter">
<encryption:pgp-encrypter-config
principal="Joe Bob
<jobbob@yahoo.com>"
publicKeyRingFileName="C:\vault\keys\joebob_public.gpg"
secretKeyRingFileName="C:\vault\keys\joebob_private.gpg"
secretAliasId="-5394156070371012997"
secretPassphrase="joebob12" />
</encryption:config>
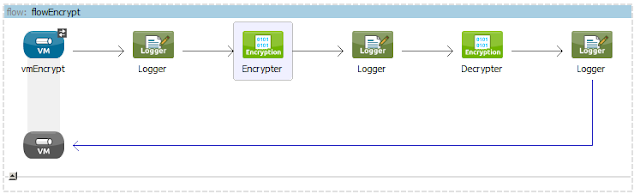
Flow Elements:
<flow name="flowEncrypt"
doc:name="flowEncrypt">
<vm:inbound-endpoint exchange-pattern="request-response"
path="queueEncrypt"
doc:name="vmEncrypt"/>
<logger message="#[payload]"
level="INFO" category="### INPUT
LOGGER ###"
doc:name="Logger"/>
<encryption:encrypt
using="PGP_ENCRYPTER" config-ref="PGP_PublicEncrypter"
doc:name="Encrypter"/>
<logger message="#[payload]"
level="INFO" category="### ENCRYPTED LOGGER
###"
doc:name="Logger"/>
<encryption:decrypt using="PGP_ENCRYPTER"
config-ref="PGP_PrivateDecrypter"
doc:name="Decrypter"/>
<logger message="#[payload]"
level="INFO" category="### DECRYPTED
LOGGER ###"
doc:name="Logger"/>
</flow>
------------------------------------------------------
./src/test/java/EncryptFlowTest.java
------------------------------------------------------
import static
org.junit.Assert.assertEquals;
import static
org.junit.Assert.assertNotNull;
import static
org.junit.Assert.assertTrue;
import
java.io.File;
import
java.io.IOException;
import
java.util.Collection;
import
java.util.HashMap;
import
java.util.Map;
import
org.apache.commons.io.FileUtils;
import
org.junit.Test;
import
org.mule.DefaultMuleMessage;
import
org.mule.api.MuleException;
import
org.mule.api.MuleMessage;
import
org.mule.api.client.MuleClient;
import
org.mule.api.transport.PropertyScope;
import
org.mule.tck.junit4.FunctionalTestCase;
public class
EncryptFlowTest extends FunctionalTestCase
{
@Test
public void testEncryptFlow () throws
MuleException
{
HashMap<String, Object> propsMap = new HashMap<String,
Object>();
MuleClient client =
muleContext.getClient();
String payloadSend = new String("The
quick brown fox jumped over the lazy dog");
MuleMessage reply = client.send
("vm://queueEncrypt", payloadSend, propsMap, 5000);
assertNotNull(reply);
assertNotNull(reply.getPayload());
assertTrue(reply.getPayload() instanceof
String );
String result =
(String)reply.getPayload();
assertEquals(result, payloadSend);
}
@Override
protected String getConfigResources()
{
return
"src/main/app/pgpexample.xml";
}
}
------------------------------------------------------
./src/test/resources/log4j.properties
------------------------------------------------------
# Default log level
log4j.rootCategory=INFO, console
log4j.appender.console=org.apache.log4j.ConsoleAppender
log4j.appender.console.layout=org.apache.log4j.PatternLayout
log4j.appender.console.layout.ConversionPattern=%-5p %d [%t] %c: %m%n
################################################
# You can set custom log levels
per-package here
################################################
# Reduce noise for Mule High
Availability
log4j.logger.com.gigaspaces=ERROR
log4j.logger.com.j_spaces=ERROR
log4j.logger.com.sun.jini=ERROR
log4j.logger.net.jini=ERROR
# CXF is used heavily by Mule
for web services
log4j.logger.org.apache.cxf=WARN
# Apache Commons tend to
make a lot of noise which can clutter the log.
log4j.logger.org.apache=WARN
# Reduce startup noise
log4j.logger.org.springframework.beans.factory=WARN
# Mule classes
log4j.logger.org.mule=INFO
log4j.logger.com.mulesoft=INFO
# Your custom classes
log4j.logger.com.mycompany=DEBUG










